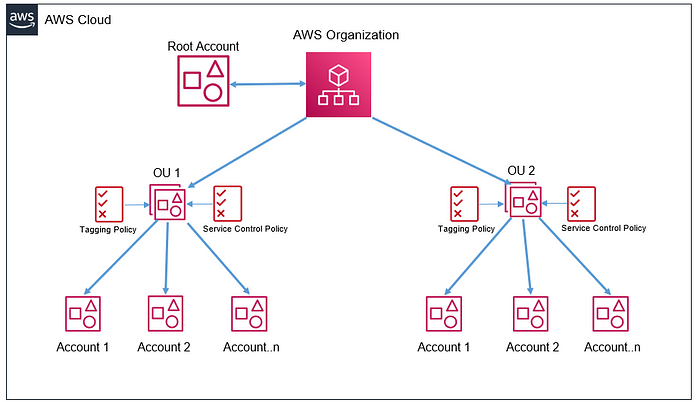
Implement AWS resource tagging strategy using AWS Tag Policies and Service Control Policies (SCPs)
AWS lets us assign metadata to the AWS resources in the form of tags. Each tag is a simple label consisting of a customer-defined key and a value that makes it easier to manage, search for, and filter AWS resources. Tagging can be an effective scaling mechanism for implementing cloud management and governance strategies. Tags can simplify attribute based access control (ABAC), as well as streamline automation/operation processes, grouping of resources for enhanced visibility, and effective cost management.
Without tags, managing your resources effectively can become difficult as you continue to utilize more AWS services. Companies of any size face the challenge of having a centralized framework or programmatic controls to enforce consistent tagging on cloud resources. This post will walk you through how to build and enrich cloud management and governance practices by utilizing AWS Organizations to create Tag Policies and Service Control Policies. We guide you in enforcing the standardization of tags, denying AWS resource creation if a specific tag is missing, and denying users from deleting existing tags on AWS resources.
Tag Policies
- Tag policies are a policy type that can help you standardize tags across resources in your AWS Organization.
- When a tag policy is applied to your AWS account, users are unable to create resources using noncompliant tags.
- You can enforce specific tag policies by choosing the option ‘prevent non-compliant operations for this tag’, and selecting the resource types that supports tag policy enforcement.
- These AWS Services and resource types support enforcement using tag policies.
Service Control Policies (SCPs)
- SCPs are a policy type that you can utilize to manage permissions across accounts in your AWS Organization.
- Using SCPs lets you ensure that your accounts stay within your organization’s access control guidelines.
- SCPs can be used along-side tag policies to ensure that the tags are applied at the resource creation time and remain attached to the resource.
Solution Overview
Policies in AWS Organizations enable you to apply additional types of management to your AWS accounts. In this solution, we enable the tag policies from the AWS Organizations, create the appropriate tag policy, and attach the policy to the target member account. Then, utilizing service control policies (SCPs), we define guardrails or set limits on the actions that an IAM user/role can conduct on the target member account. Using Tag policies and SCPs would not incur any additional charge.
This solution covers detailed steps, including reusable policy templates to:
- Apply and enforce a standardized tagging policy during AWS resource creation.
- Deny AWS resource creation if a specific tag is missing.
- Deny users from deleting specific tags on AWS resources.
For further reading, check my blog @